WannaCry, variants could escalate as many users yet to apply patches
Cyber Security Agency confirms no Singapore critical sectors hit; less than US$50,000 in ransom believed to have been paid so far
Singapore
OVER the past few days, country music star Keith Urban's song Tonight I wanna cry must have been trending among the normally taciturn geeks who protect our computers and IT systems, with the WannaCry virus quickly becoming the largest global ransomware attack, affecting an estimated 200,000 computers in 150 countries, including many in Singapore like the digital directories of Tiong Bahru Plaza and White Sands shopping centre.
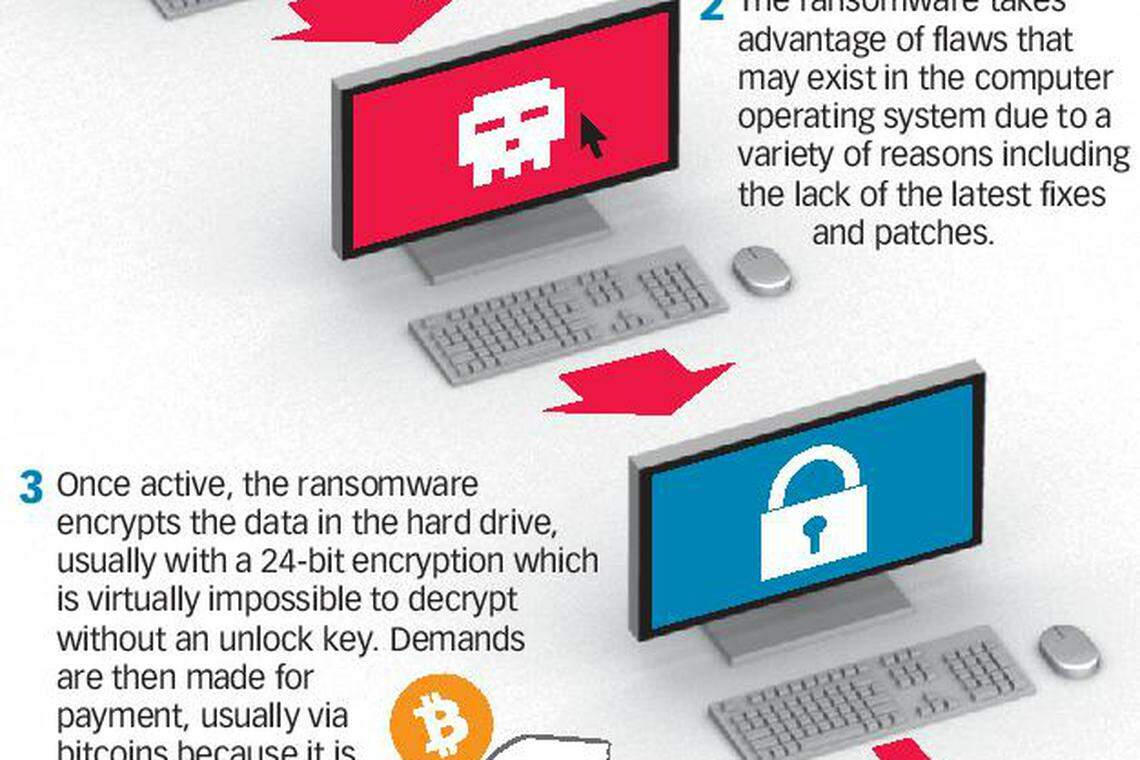
Ransomware is a type of malicious software that infects a computer and restricts users' access to it until a ransom is paid, usually in bitcoins, to unlock it.
In Singapore, apart from the two shopping malls, a retail shop is another known victim. A spokesperson for the malls has clarified that no vital data was affected and technicians were fixing the problem which appeared to have affected 12 digital kiosks in the malls. MediaOnline, which supplied the digital signage to the two malls, was last reported to have disconnected its system from the kiosks while a solution patch was being installed.
The spokesperson said no sensitive information in the mall directories was leaked, and hackers did not receive any money or bitcoin.
The Cyber Security Agency (CSA) of Singapore's SingCERT has advised the business owner of the retail shop on remedial measures to clean up its systems.
Dan Yock Hau, CSA director, National Cyber Incident Response Centre, said in a statement on Monday: "As of this afternoon, no Critical Information Infrastructure (CII) has been affected. CSA's SingCERT has received three calls today from businesses and members of the public on the WannaCry ransomware. However, these were queries on how to prevent a ransomware attack rather than to recover from it."
He added that CSA would continue to monitor the situation closely and was working with the CII sectors to check on their state of readiness. "We are also tracking other sources of intelligence and have reached out to offer assistance to those that were brought to our attention."
Globally, first computers to be hit were those of the British public healthcare system on Friday with hospitals being locked out of their computers with the demand that they pay a ransom before they could get back their computers. Many hospitals in Britain had to turn away patients. Apart from that, from what is known till now, other high profile victims include international shipper FedEx, train systems in Germany, a Spanish telecommunications company and a Russian government ministry.
The attack could have been even more severe if it had not been for the fact that it was "accidentally" stopped by a security expert in UK on Friday. The expert inadvertently found a "kill switch" in the virus code and activated it, thus limiting its spread.
However, the respite is likely to be short-lived. Gartner's principal research analyst Anmol Singh told The Business Times that the virus is likely to spread further and infect more computers "with older and unlicensed versions of Microsoft Windows".
"What's concerning about this ransomware is its worm-like characteristic, enabling it to spread faster across vulnerable targets than previous ransomwares, making it one of its kind."
Mr Singh added that while Microsoft has released fresh updates to prevent this malware from spreading and causing any further damage, "the hackers have already begun to alter the malware's source-code so as to ensure it's free of any kill switch and, therefore, is less likely to be identified and killed easily".
Sanjay Aurora, Asia Pacific MD of security company Darktrace added: "The automatic spreading of the infection suggests that we are not yet out of the woods. As different countries return to work and switch on their devices (on Monday, local time), the threat level rises once more."
Speaking to BT, Nick Savvides, security advocate, Symantec Asia Pacific and Japan (APJ), said the WannaCry attack and variants of it have the "potential to escalate", as many organisations still haven't applied the patches to prevent the automatic spread.
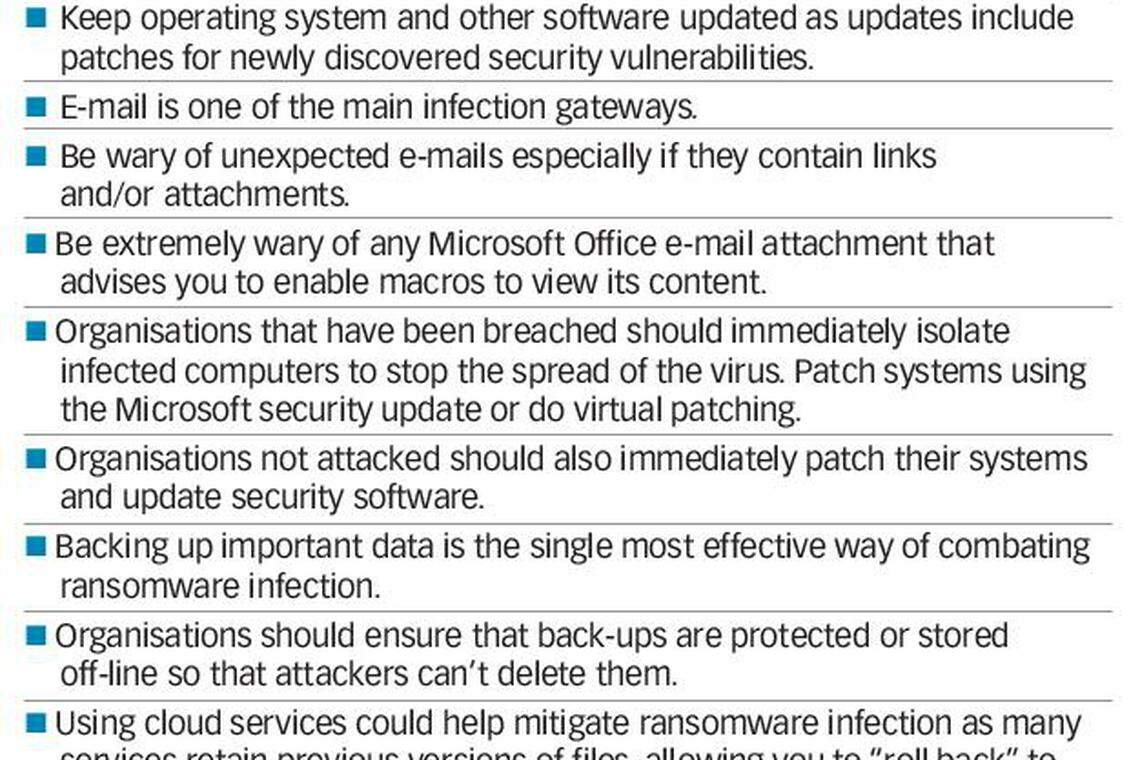
"The best defence is to ensure the operating systems and security software are up to date and importantly educate users to exercise caution and understand the threats."
Agreeing with Mr Savvides, Irdeto's director of technology, Ben Gidley, said the attack "is the latest example of organisations not taking cybersecurity serious enough".
Saying that these attacks could have easily been avoided if organisations had their systems patched properly, Mr Gidley noted that a patch was issued on March 14 to fix that vulnerability.
Rather ironically, the hackers appeared to have exploited a flaw in Microsoft's Windows operating system first discovered by the National Security Agency (NSA) of the US. The vulnerability and tools to exploit it were stolen from NSA by a hacking group called Shadow Brokers who made them public in April.
Hackers behind the exploit reportedly demanded US$300 for unlocking individual computers. Once the virus hit globally, some experts had estimated that the hackers could make up to as much as US$1 billion in "ransom". Surprisingly, according to a Twitterbot that tracks the ransom payments in real time, only US$42,000 has been paid to date for what is the largest ransomware attack in history.
However, Symantec's Mr Savvides noted that ransomware is "extremely profitable for cyber-criminals and we expect this to continue". He added that the profitability of ransomware has attracted new cyber-criminals to it.
Symantec research showed that globally ransomware attacks grew grew 36 per cent in 2016 to 463,841, from 340,665 in 2015. The average ransom per victim grew 266 per cent to US$1,077 in 2016, from US$294 in 2015.
To a question on how long this particular threat would continue, Trend Micro's Asia Pacific regional solutions architect, Tarun Gupta, told BT that cybercriminals will never stop mounting attacks. "It's an ongoing battle for the industry. With such vulnerability in the open, there will be a large number of unpatched systems out there, so potentially the WannaCry attack could continue. However, even if it's not WannaCry, it could be another ransomware variant, or an advanced persistent threat (APT) attack," Mr Gupta said.
William Woo, Singapore Telecommunication's MD, Enterprise Data and Managed Services, Group Enterprise, told BT that to be the world's first Smart Nation, Singapore first "has to be a cyber safe nation".
"Before a single product or solution is deployed, we have to ensure that it is already designed and built with cybersecurity in mind."
He added that cybersecurity is an issue that no single entity can deal with on its own as the range of cyber threats and cybersecurity solutions are too complex to be managed alone. "Therefore, companies need to collaborate with the relevant government agencies such as the CSA, and industry players who can support them with comprehensive managed security services and global threat intelligence as part of their overall service offerings."
READ MORE:
KEYWORDS IN THIS ARTICLE
BT is now on Telegram!
For daily updates on weekdays and specially selected content for the weekend. Subscribe to t.me/BizTimes
Technology
'Harvesting data': Latin American AI startups transform farming
After long peace, Big Tech faces US antitrust reckoning
Tech’s cash crunch sees creditors turn ‘violent’ with one another
Tech millionaires chase billionaire tax shields with ‘swap fund’
Elon Musk’s Starlink profits are more elusive than investors think
Hollywood animation, VFX unions fight AI job cut threat
